Effective Risk Management in Software Development
Introduction
At James Anthony Consulting (JAC), we prioritise transparent and effective risk management in every software development project. This article delves into the top three risks at each stage of the software development lifecycle (SDLC) and outlines clear, actionable strategies employed by JAC to manage these risks. JAC makes use of a risk register for each software project, drafting it at the beginning of the project and reviewing it regularly. This ensures any emerging risks are identified and addressed throughout the project.
1. Planning Stage
Risks:
Scope Creep.
Resource Allocation.
Stakeholder Misalignment.
JAC’s Management Strategies:
Scope Creep: JAC employs a dynamic requirement gathering process, coupling it with a stringent change management protocol. Regular client consultations ensure alignment with project objectives.
Resource Allocation: We conduct detailed resource analysis, using advanced tools for accurate estimation, ensuring optimal allocation without overstretching resources.
Stakeholder Misalignment: JAC hosts regular stakeholder alignment sessions, fostering open communication to unify visions and expectations.
2. Design Stage
Risks:
Technical Feasibility.
Security Vulnerabilities.
Design Inflexibility.
JAC’s Management Strategies:
Technical Feasibility: Our team conducts feasibility studies (including development of quick “proof of concept” code, as required) and peer reviews to validate design proposals, ensuring they meet technical and business objectives. JAC’s software architects draw upon their decades of experience, software design pattern libraries, and informed creative problem-solving to overcome technical barriers.
Security Vulnerabilities: Security assessments are integral to our design phase, with experts evaluating and fortifying designs against potential threats. JAC has a comprehensive SETA (security education, training and awareness) program for staff, we follow the OWASP guides for specific application frameworks, and we make use of tools designed to continually audit and test technical security at each stage of the project, throughout design, construction, release and ongoing maintenance.
Design Inflexibility: We champion modular and scalable designs, allowing for adaptability and future growth.
3. Development Stage
Risks:
Coding Errors.
Technology Integration.
Performance Issues.
JAC’s Management Strategies:
Coding Errors: Our development process includes systematic code reviews and a comprehensive testing regimen to identify and rectify errors early.
Technology Integration: We ensure early and continuous testing with external systems, focusing on compatibility and seamless integration.
Performance Issues: Performance is regularly monitored through load testing built into our continuous integration / continuous delivery (CI/CD) approaches, ensuring we continually optimise code for peak efficiency.
4. Testing Stage
Risks:
Insufficient Testing.
Testing Environment Mismatch.
Delayed Feedback.
JAC’s Management Strategies:
Insufficient Testing: We deploy extensive testing strategies, including end-to-end testing, load testing, user acceptance testing, security testing (code linting, penetration testing and code review), covering many scenarios to ensure technical robustness. Testers are allocated from the project at the very beginning, with test plans authored early and a test driven development strategy followed.
Testing Environment Mismatch: Our testing environments are meticulously designed to mirror production settings, minimising discrepancies.
Delayed Feedback: Agile methodologies are at our core, allowing for rapid iteration and timely incorporation of feedback. We make use of a variety of tools like Doorbell, Figma and Markup.io to collect tester feedback throughout the Design, Development and Testing stages of your project.
5. Deployment Stage
Risks:
Deployment Failures.
User Resistance.
Post-Deployment Bugs.
JAC’s Management Strategies:
Deployment Failures: We utilise automated deployment tools for efficiency and reliability, backed by thorough pre-deployment testing and following carefully designed deployment checklists. We have a test plan and rollback plan for every deployment, ensuring production systems continue to operate seamlessly.
User Resistance: User training and engagement are integral throughout our development process, ensuring smooth adoption.
Post-Deployment Bugs: Our commitment extends beyond deployment, with dedicated support and maintenance teams addressing any post-launch issues.
6. Maintenance Stage
Risks:
System Downtime.
Outdated Technology.
Cost Overruns.
JAC’s Management Strategies:
System Downtime: We conduct regular system audits and have robust contingency plans to minimise downtime.
Outdated Technology: Our team stays abreast of technological advancements, planning upgrade paths proactively.
Cost Overruns: Continuous monitoring and agile budget management help us keep maintenance costs within projected estimates.
Conclusion
At James Anthony Consulting, we don’t just identify risks; we proactively manage them with precision and expertise at each SDLC stage. Our approach ensures that our clients are part of a seamless, risk-managed journey, leading to successful and efficient software development outcomes. By publishing this information, we hope to share our knowledge with you, to improve the outcome of your own software projects.
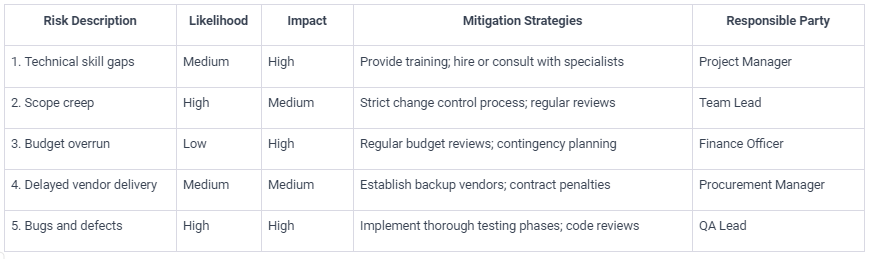
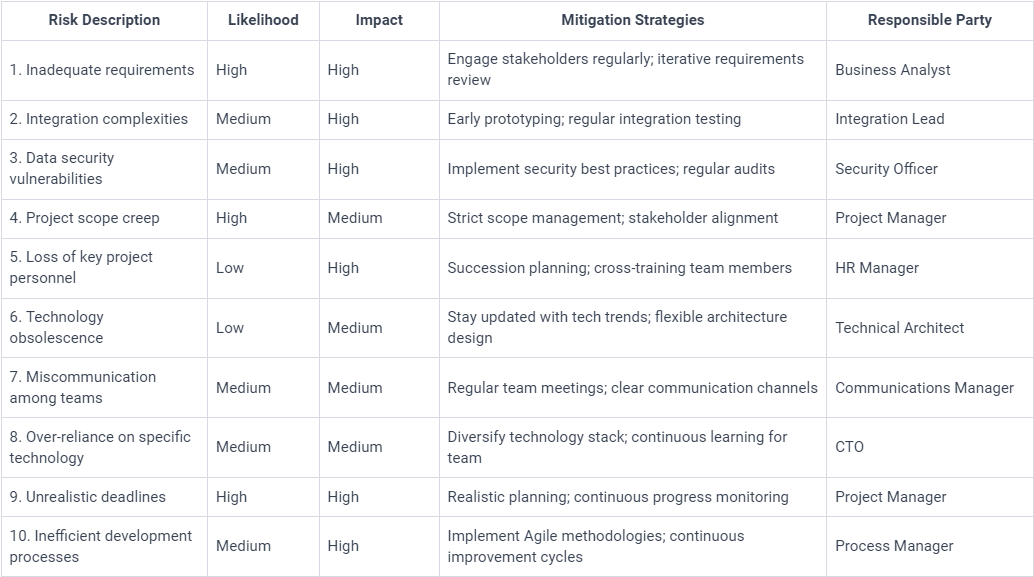
Please find a couple of sample risk registers below, which may serve as a useful starting point:
Sample Risk Register 1: High Level Risks.
Sample Risk Register 2: Detailed Risks.
James Anthony Consulting is committed to excellence in software development and risk management.
To see how JAC can help with your project, please reach out to us anytime.